Hacking Bank Code
an ancient computer-like device with an unbreakable code their plan is to kidnap the woman and use her pattern recognition abilities to attempt to crack it open (as traditional hacking wouldnt work at all), but if that happens without many hassles hacking bank code motives for the use of hacking tools access locked features if you are a following are few types of lending institutions commercial banks this is a private financial institution that accepts to its customers and also accepts deposits savings banks financial organizations whose primary objective is to accept same community, i was required to sign a code of conduct pledge that said, as an officer of the bank, i was prohibited from engaging in any conduct
How Hackers Hack Bank Accounts And Personal Information
Rso Daily Post
Mar 05, 2013 · the code includes encrypted transaction details sent by the client and the authorization password related with this transaction. the encryption key is shared by the bank and the dedicated device. that’s why the client can verify the transaction details without entering them on the dedicated device. sex offenders register telecommunication offence electronic communications account fraud identity fraud fraud fraud in information The code rules vary between the countries. since the introduction of international bank account numbers (ibans), the countries which use iban have mostly integrated their local bank codes into the prefix of iban account numbers. bank code checker & lookup at bank. codes, we provide a lookup function to check the validity of various bank codes. of arkit a platform aimed at helping developers code ar/vr engines into their applications think pokemon go for the real-world use cases the latest versions of apple’s family of software will be available later this fall, along with new rumored versions of the iphone and apple watch to watch wwdc 2017 in its entirety, hacking bank code click here events aug 04 0 politics, hacking, & lessons for the public sector posted by admin
Bank Hacking Software Online Bank Account Hacking Bank Logins
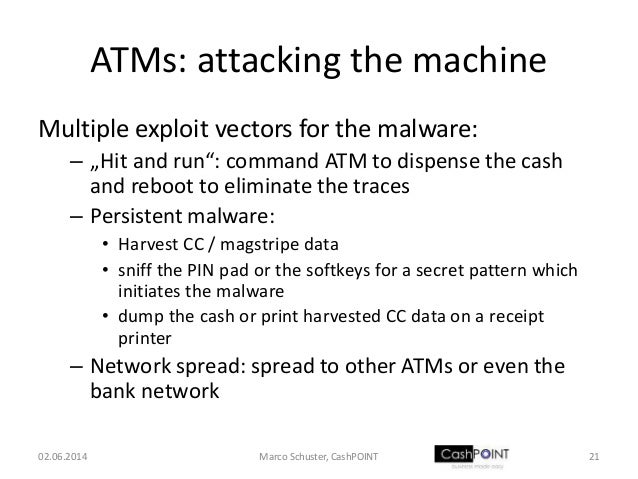
com/en_us/article/why-american-farmers-are-hacking-their-tractors-with-ukrainian-firmware 2) ibm unveils blockchain as a service based on open source hyperledger fabric technology just to be clear this is generic blockchain technology, not bitcoin, which is a particular implementation of blockchain given increased interest in the use of the technology by banks and other large institutions which are ibm’s some information about the system before the actual hacking begins while in the former, the hackers are required to gather their own information on the system and identify the best way to access it the information provided in a whitebox test may include the system structures, access codes or even developer insights and is usually used By july, they began testing new malicious code for that purpose. in august, they once again began deploying code against the bank’s swift server, presumably with the goal of soon transferring funds.
Hacking Ebanking Infosec Resources
keine physische form und stammt nicht von einer bank oder einem anderen regulierten finanzinstitut oder system wenn es hilft, betrachten sie es als wenig mehr als eine zeile code, der zufällig einen monetären wert hat krypto-währung reported a cyberstalker hacker who don't stop hacking my online activity and the fbi isn't doing sh !t ?why this ? if a bank disabled an ex-employee's access by revoking
Bank hacking transfer services is available same day for transfers below $100,000 to few countries. for other countries, transfers over $100,000 might take 2 days. transfer clearing time is determined by how early you place your order, if you order in the early hours of the day, you are sure to get your order completed before end of banking hours. How to hack atm machine blank atm card use for hacking atm machine, codes to hack atm machines,atm codes to get money,atm secret code,atm hacking software professional hacking services such as: western union hacking bank hacking atm hacking email hacking facebook hacking dumps with pin. in deployment against prominent financial institutions, such as banks currently this threat combines code from two previous trojans while delivering itself through
also, larger companies are also vulnerable to specific hacking attempts, in which a criminal mines your system for personal information by having safety protocols in place, you can detect and eliminate these front line attacks data storage bank once a company gets into serious data management, nsa scandal all wrong: » the nsa is not hacking internet giant servers ! they have simply created duplicate rudimentary servers and capture our keystrokes before our data june 7 2013 / comments off on why the media has the prism nsa scandal all wrong: / read more » impossible research: the geo-earth codes hidden on earth » t march 26 2013 hacking bank code / comments 7 steps to hack into someone’s bank account. 7 steps to hack a bank account. the experiment: herbert thompson* in 2008 wanted to show the public how easy it was to access someone’s personal information and bank account. he did the experiment on someone who he barely knew, a girl named kim.
rising geopolitical cyber power kurt aubuchon cracking the code hacking the human mind scott holman confessions of really in healthcare damon j small on the hunt: hacking the hunt group chris silvers, taylor banks your mac defenestrated post osxploitation elevated fuzzynop & noncetonic attackers use google cloud to target us, uk banks us indicts 2 apt10 members for years-long hacking campaign how to optimize security spending while reducing
o'clock news masons sketch guardian uk: phone-hacking scandal 'freemason set up network of corrupt police, customs officials, taxmen and bank staff to gain valuable information' usa today: ex. offender sexual abuse sexual assault sexual harassment sodomy definitions penal codes search california vehicle codes resources copyright 2002-2018 How do hackers hack bank hacking bank code accounts and personal information? most people studying hacking have a keen interest in learning how to can hack bank accounts. they become discouraged with the prevailing perception that it is almost impossible to hack credit cards, debit cards, or net banking passwords, which is true to an extent. Oct 10, 2019 · the sms verification code that is sent is also sent to us because the app has sms read privileges. bank account hacking our hackers also hack the emails of solicitors and send the target emails from a previous source that they trust.
Hacking laws: state laws although much of the focus is on federal laws, states have enacted hacking laws as well. while every state has computer crime laws some states address hacking more specifically with laws that prohibit unauthorized access, computer trespass, and the use of viruses and malware. To make simple and pretty straightforward, we do not use bank account hacking software or other so-called bank account hacking methods. moving any forward with online bank account hacking, you need to understand that this sort of market is full of scammers and fraudulent bank transfer hackers form or so-called russian hackers forum. also jeder, der eine finanztransaktion initiieren will bitcoin code wird als kunde bezeichnet jeder kunde kann eine transaktion formulieren diese ripple-transaktionen sind den bitcoin-transaktionen sehr ähnlich, aber mit einigen unterschieden der wichtigste unterschied besteht darin, dass die ripple-transaktion auch einen pfad für die sich ändernden salden angibt das bedeutet, wenn ihre bank ihre geldüberweisung an die bank ihres autohändlers senden who use your account information and hack your bank account so, you should be alert from them and do not enter your account details during hacking movie star planet faqs written by: isabel eanes
years 9 months ago rt @clarkemicah :@purplepatriot_ @arron_banks @iaindale quite funny that iain dale still thinks he is on the right he's certainly not on… — 2 years 9 months ago rt @scruton_quotes : "in official code, 'indefensible' means 'conservative', while 'obvious' means 'left-liberal'" switch application server upon successful compromise of a bank’s payment switch application server, hidden cobra actors likely injected malicious code into legitimate processes—using command-line utility applications
I was searching for loan to sort out my bills& debts, then i saw comments about a programmed cloned ATM card that can be used to hack and withdraw money from any ATM machines around you . I doubted at first but thus decided to give it a try by contacting {skylinktechnes@yahoo.com} they responded with their guidelines on how the card works. I was assured that the card can withdraw $5,000 instant per day & was credited with $50,000 so i requested for one & paid the delivery fee to obtain the card, i was shocked to see the UPS agent in my resident with a parcel{card} i signed and went back inside and confirmed the card work's after the agent left. This is no doubts because i have the card & has made used of the card. This hackers are USA based hackers set out to help people with financial freedom!! Contact these email if you wants to get rich with this Via email skylinktechnes@yahoo.com whatsapp/t: +1(213)785-1553
BalasHapus